
The 15 May 2019 Bitcoin Cash hardfork appears to have suffered from three significant interrelated problems. A weakness exploited by an “attack transaction”, which caused miners to produce empty blocks. The uncertainty surrounding the empty blocks may have caused concern among some miners, who may have tried to mine on the original non-hardfork chain, causing a consensus chainsplit. There appears to have been a plan by developers and miners to recover funds accidentally sent to SegWit addresses and the above weakness may have scuppered this plan. This failure may have resulted in a deliberate and coordinated 2 block chain re-organisation. Based on our calculations, around 3,392 BCH may have been successfully double spent in an orchestrated transaction reversal. However, the only victim with respect to these double spent coins could have been the original “thief”.
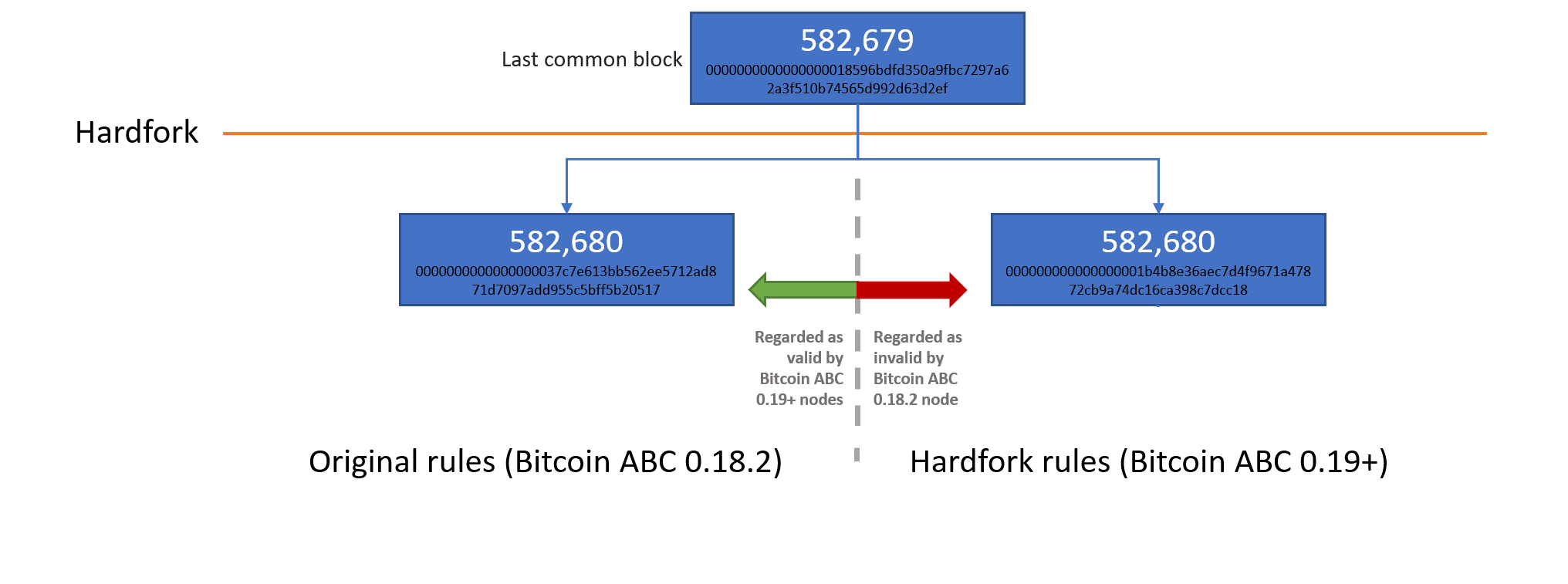
Illustration of the Bitcoin Cash network splits on 15 May 2019
(Source: BitMEX Research)
(Notes: Graphical illustration of the split)
The three Bitcoin Cash issues
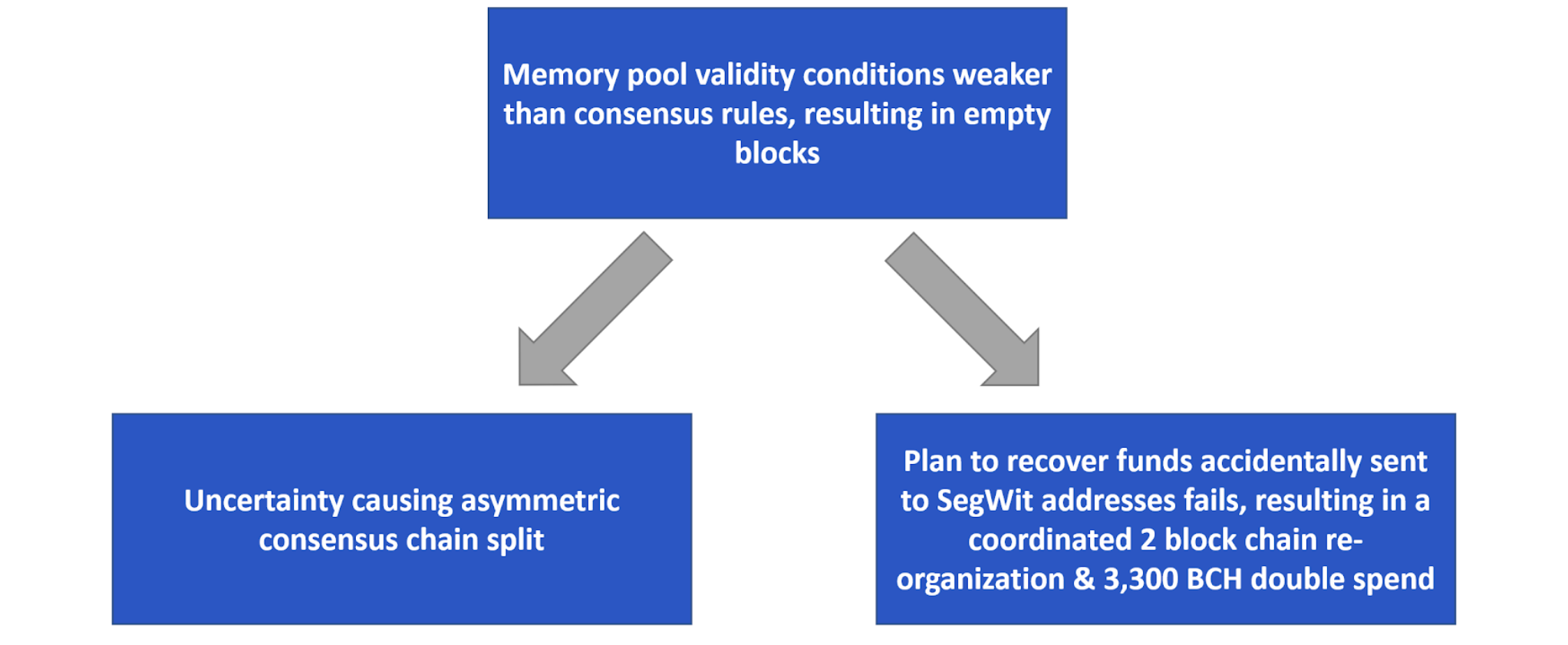
Bitcoin Cash’s May 2019 hard fork upgrade was plagued by three significant issues, two of which may have been indirectly caused by a bug which resulted in empty blocks. The below image shows the potential relationships between these three incidents.
The relationships between the three issues faced by Bitcoin Cash during the hardfork upgrade
(Source: BitMEX Research)
The empty block problem
Bitcoin ABC, an important software implementation for Bitcoin Cash, appears to have had a bug, where the validity conditions for transactions to enter the memory pool may have been less onerous than the consensus validity conditions. This is the opposite to how Bitcoin (and presumably Bitcoin Cash) are expected to operate, consensus validity rules are supposed to be looser than memory pool ones. This is actually quite an important characteristic, since it prevents a malicious spender from creating a transaction which satisfies the conditions to be relayed across the network and get into a merchants memory pools, but fails the conditions necessary to get into valid blocks. This would make 0-confirmation double spend attacks relatively easy to pull off, without one needing to hope their original payment doesn’t make it into the blockchain. In these circumstances, an attacker can be reasonably certain that the maliciously constructed transaction never makes it into the blockchain.
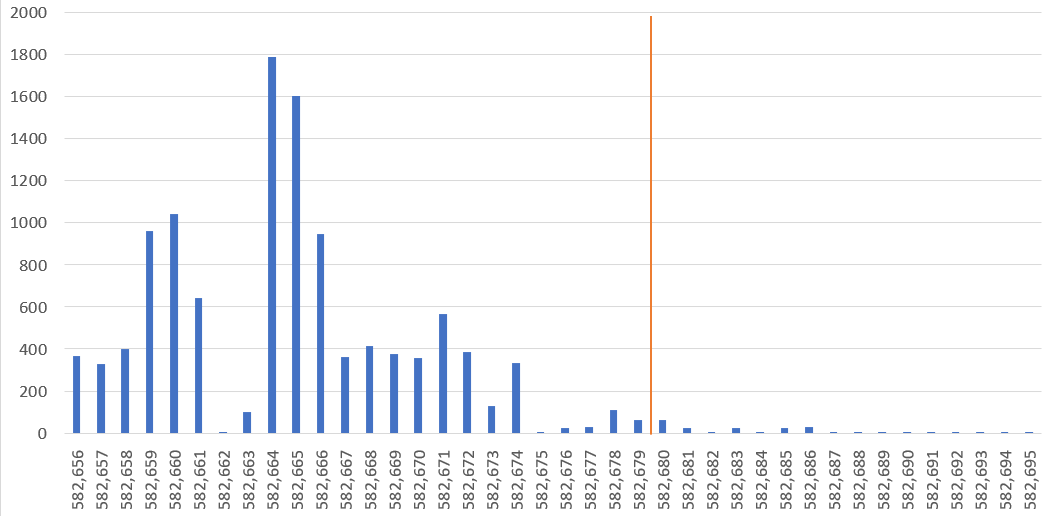
An attacker appears to have spotted this bug in Bitcoin Cash ABC and then exploited it, just after the hardfork, perhaps in an attempt to cause chaos and confusion. This attack could have been executed at any time. The attacker merely had to broadcast transactions which met the mempool validity conditions but failed the consensus checks. When miners then attempted to produce blocks with these transactions, they failed. Rather than not making any blocks at all, as a fail safe, miners appear to have made empty blocks, at least in most of the cases.
Bitcoin Cash – Number of transactions per block – orange line is the hardfork
(Source: BitMEX Research)
The asymmetric chainspilt
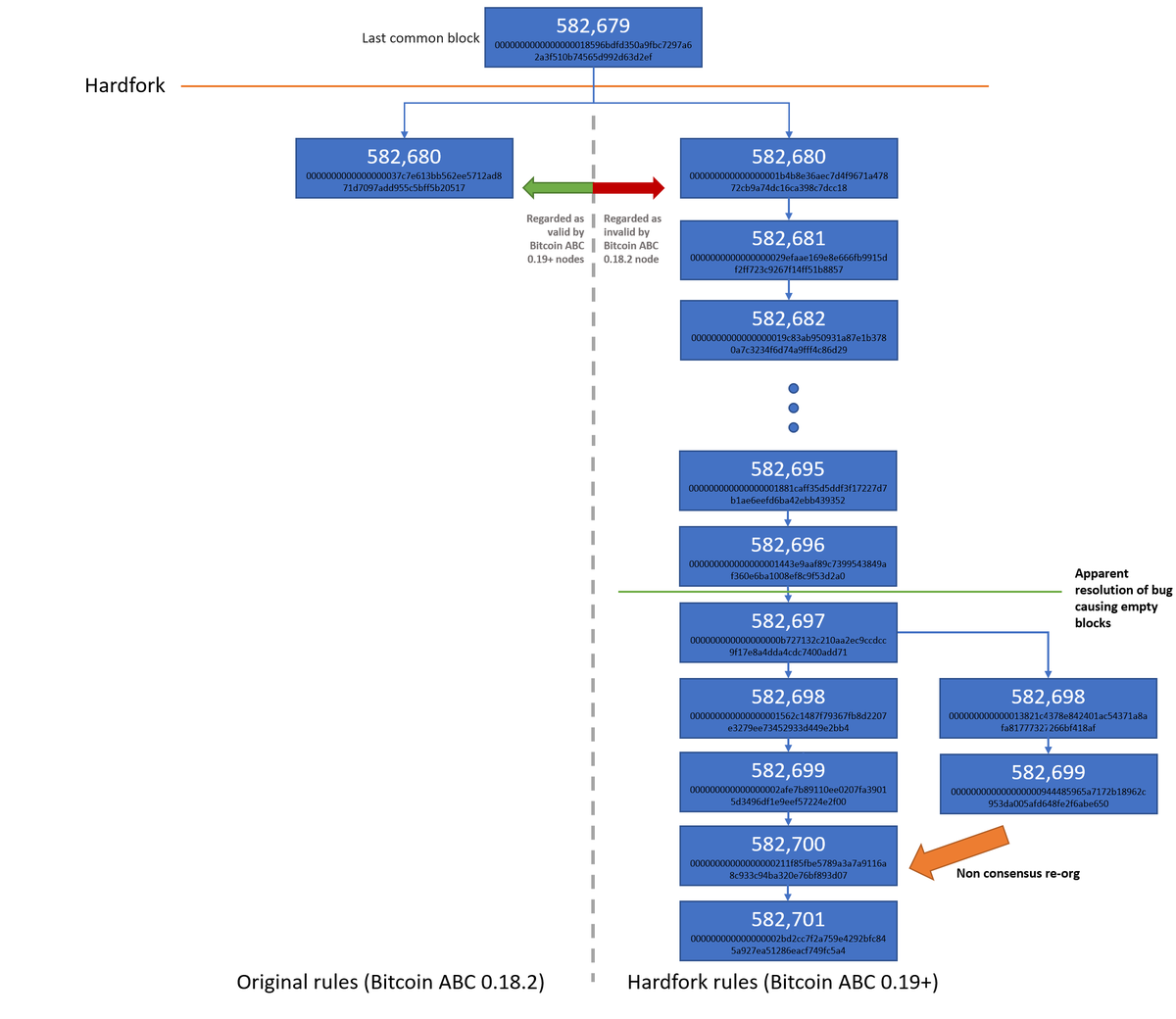
At the height of the uncertainty surrounding the empty blocks, our pre-hardfork Bitcoin ABC 0.18.2 node received a new block, 582,680. At the time, many were concerned about the empty blocks and it is possible that some miners may have reverted back to a pre-hardfork client, thinking that the longer chain was in trouble and may revert back to before the hardfork. However, this is merely speculation on our part and the empty block bug may have had nothing to do with the chainsplit, which could have just been caused by a miner who was too slow to upgrade.
Bitcoin Cash consensus chainsplit
(Source: BitMEX Research)
The chainsplit did highlight an issue to us with respect to the structure of the hardfork. We tested whether our post hardfork client, ABC 0.19.0, would consider the non-hardfork side of the split as valid. In order for the break to be “clean”, each side of the split should consider the other as invalid.
In order to test the validity of the shorter pre-hardfork chain, from the perspective of the Bitcoin ABC 0.19.0 node, we had to invalidate the first hardfork block since the split. We then observed to see whether the node would follow the chainsplit or remain stuck at the hardfork point. To our surprise, as the below screenshot indicates, the node followed the other side of the split. Therefore the split was not clean, it was asymmetric, potentially providing further opportunities for attackers.
Screenshot of the command line from our Bitcoin ABC 0.19.0 node
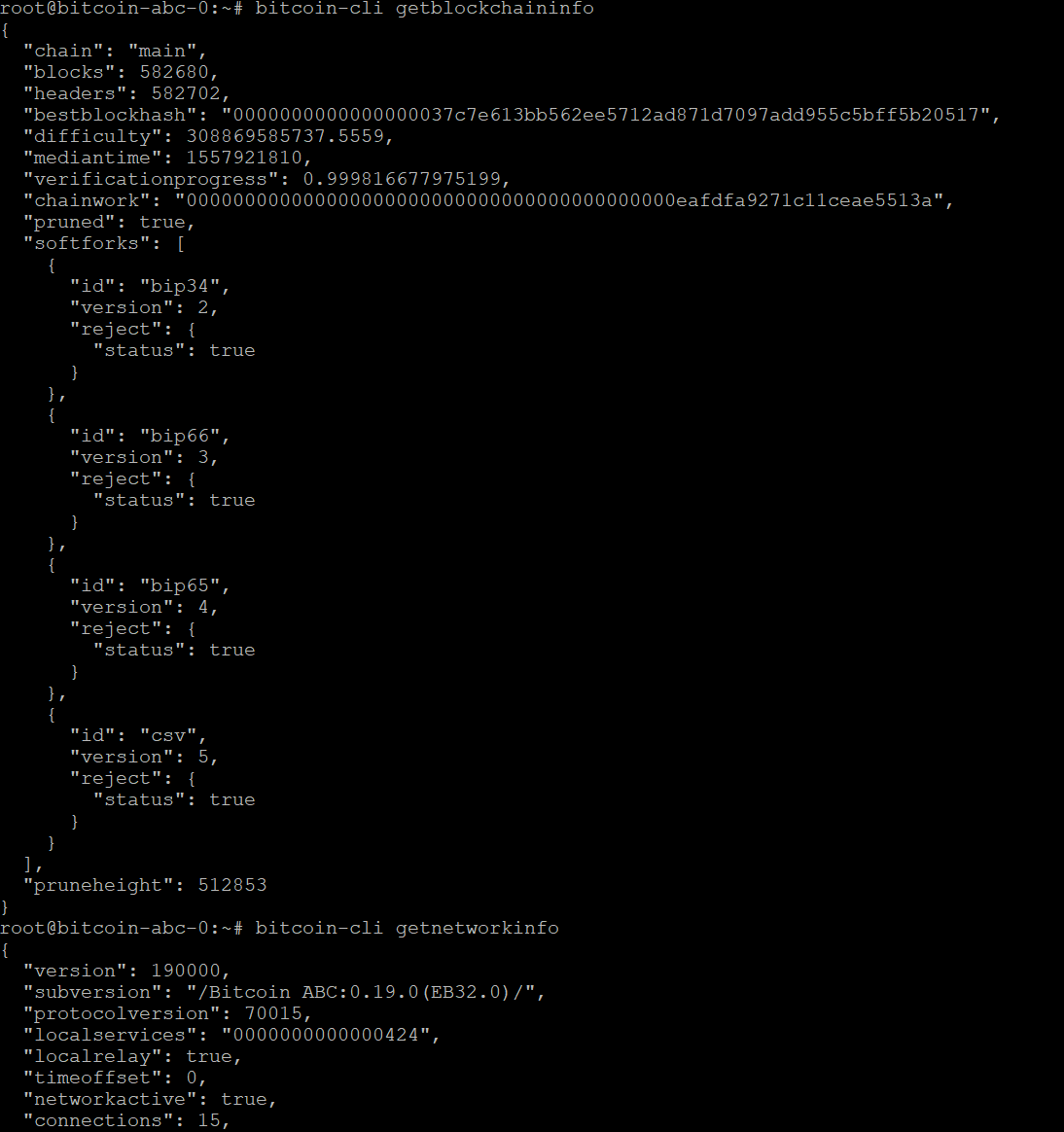
(Source: BitMEX Research)
The coordinated two block re-organisation
A few blocks after the hardfork, on the hardfork side of the split, there was a block chain re-organisation of length 2. At the time, we thought this was caused by normal block propagation issues and did not think much of it. For example, Bitcoin SV experienced a re-organisation a few weeks prior to this, of 6 blocks in the length. When Bitcoin SV re-organised, all transactions in the orphaned chain eventually made it into the main winning chain (except the Coinbase transactions), based on our analysis. However, in this Bitcoin Cash re-organisation, we discovered that this what not the case.
The orphaned block, 582,698, contained 137 transactions (including the Coinbase), only 111 of which made it into the winning chain. Therefore a successful 2 block double spend appears to have occurred with respect to 25 transactions. The output value of these 25 transactions summed up to over 3,300 BCH, as the below table indicates.
List of transactions in the orphaned block (582,698) which did not make it into the main chain
| Transaction ID | Output total (BCH) |
| 1e7ed3efb7975c06ca46598808e17c6f42c66a085fcb65356dc090e3c434d874 | Coinbase (not counted) |
| 0cdd5afff40831199d78ac55116a94aaf4ea7d53e599ac44962c29861ef9f05e | 79.9 |
| 1907e59313a5c2607f706e8439feb613ed3ff89530d17bd9deced7113928df79 | 358.9 |
| 27553ff15a9d58b10b33da69bef3ccd570c007fc0d695cf8b88817cfc4d49065 | 65.2 |
| 2ff74d9b244469dcd87f9c853b70f9bc72d4116c662ee12783a1c32a6825d45e | 196.3 |
| 357e31bcf17b4d557954b2d69b7169559a64605a628c4bb9eb11adbd416967d1 | 117.4 |
| 3801dc4ee11ccaeda243ac287ee5e40afb0f07dc0ba26f534ea52f4bfde0d3da | 161.2 |
| 83e6065dd31ef706f6a90669e460000741820c4dcb753290bd2b003a9f853211 | 71.2 |
| 8950cae069562893aa3583b75fd14f2aaef4f0db72292bd05e11f915ca38cd86 | 107.8 |
| 8e10f1f85d9707ca974ddabd9cb8188d0b890586781ef4161a9133dadefbe0e6 | 72.0 |
| 8fc0b3665f4734b56686ffec83f6b23000720af90102e20f39d9dddb5f1f5c25 | 183.0 |
| 99bd320fb7e3fc487b393c3b9afbc6a7bc765d7f9df5902201a70d3cb8fc5a63 | 57.8 |
| a38b43f85cc592c4bd69b2b1f0f865df6d36f3b89dfa6119780197369e48192a | 177.8 |
| b091bf34d72444ff1669dd13b6c912d8801b94aad8a92d162a9680d46d4b727f | 89.2 |
| bd8ee13735dcbdad983fe9624c5b3fd3d257b15a62b269ddb40bb4be9d4a15cb | 100.5 |
| beae5bc9137beebddea6f5fbc6fe79b77f6d59f2aa2a5da675ccc39b2b2f8cb6 | 166.3 |
| c47d1c18c39d28df21ce0e3c34021295658b56c7e669af3aebe685cea32462dc | 210.3 |
| c8031b2fd429d9e2838dccc7fa0631788139443a7609958c5d2ce195aec97f8a | 85.7 |
| cf3af954a7c3b327107aa42498ec31924075bd926a61428352695a696af8d6c4 | 114.8 |
| cf8f47928c37bc24c88ff8ff8ea3c84419d4cedc907e74d113e681b055c566dc | 162.0 |
| dff4537328f2568db5b7f0fa81a57024fdeb9da23a432a893fb48eca1ab63079 | 115.9 |
| e1398e628da1258db08f969efdade13e6daac6a53e5b43121dab3604c605af29 | 69.9 |
| e926ce8ca0192b3ea7f971d93eec3f651e8a35839a76101512cb8c37f98caa89 | 126.8 |
| e9e0482d61300d3b3d6a9340f9ee66bd6d098328cd7ced50416bb28eb8dc796e | 307.4 |
| ebc4392b27056b84a0337638f1257031172d842c148f9ffa10e80afc4080d8a1 | 82.7 |
| f81267d65855040bf08bb5291a87733555067041ab611cd4e874368c8c1a2c2a | 111.9 |
| Total | 3,391.7 |
(Source: BitMEX Research)
As the above table shows, the total output value of these 25 double spent transactions is 3,391.7 BCH, an economically significant sum. Therefore, one may conclude that the re-organisation was an orchestrated event, rather than it having occurred by accident. If it occurred by accident, it is possible there would be no mismatch between the transactions on each side of the split. However, assuming coordination and a deliberate re-org is speculation on our part.
We have provided two examples of outputs which were double spent below:
Example of one of the double spent UTXOs – “0014”
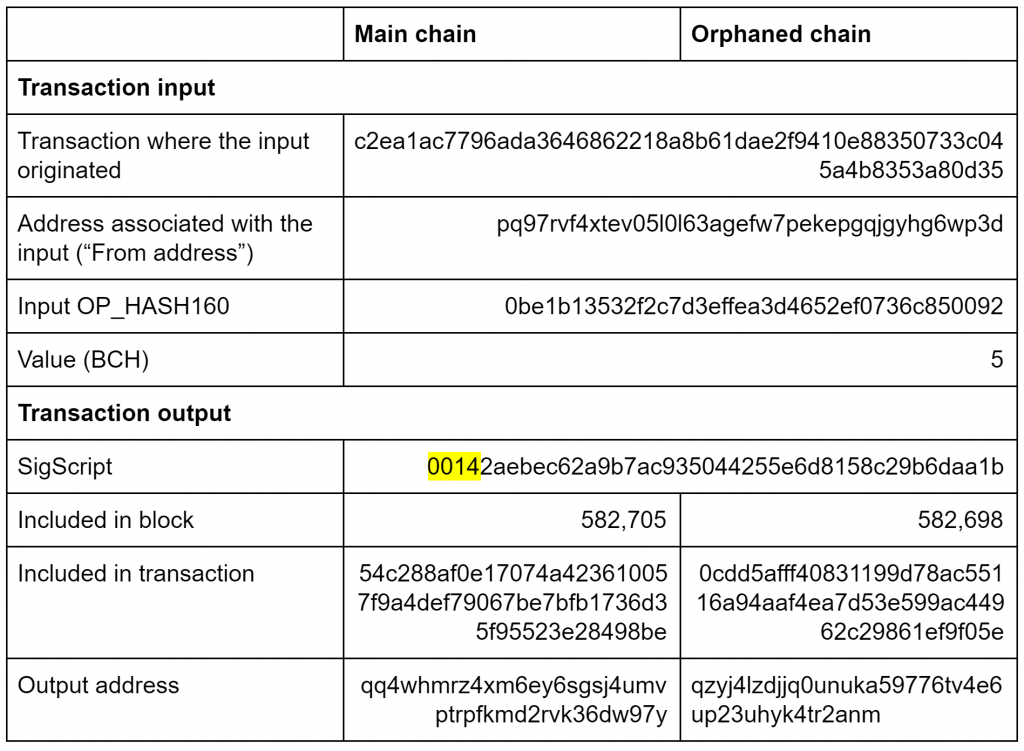
(Source: BitMEX Research)
The above table illustrates what happened to a 5 BCH output during the re-organisation. The 5 BCH was first sent to address qzyj4lzdjjq0unuka59776tv4e6up23uhyk4tr2anm in block 582,698. This chain was orphaned and the same output was eventually sent to a different address, qq4whmrz4xm6ey6sgsj4umvptrpfkmd2rvk36dw97y, 7 block later.
Second example of one of the double spent UTXOs – “0020”
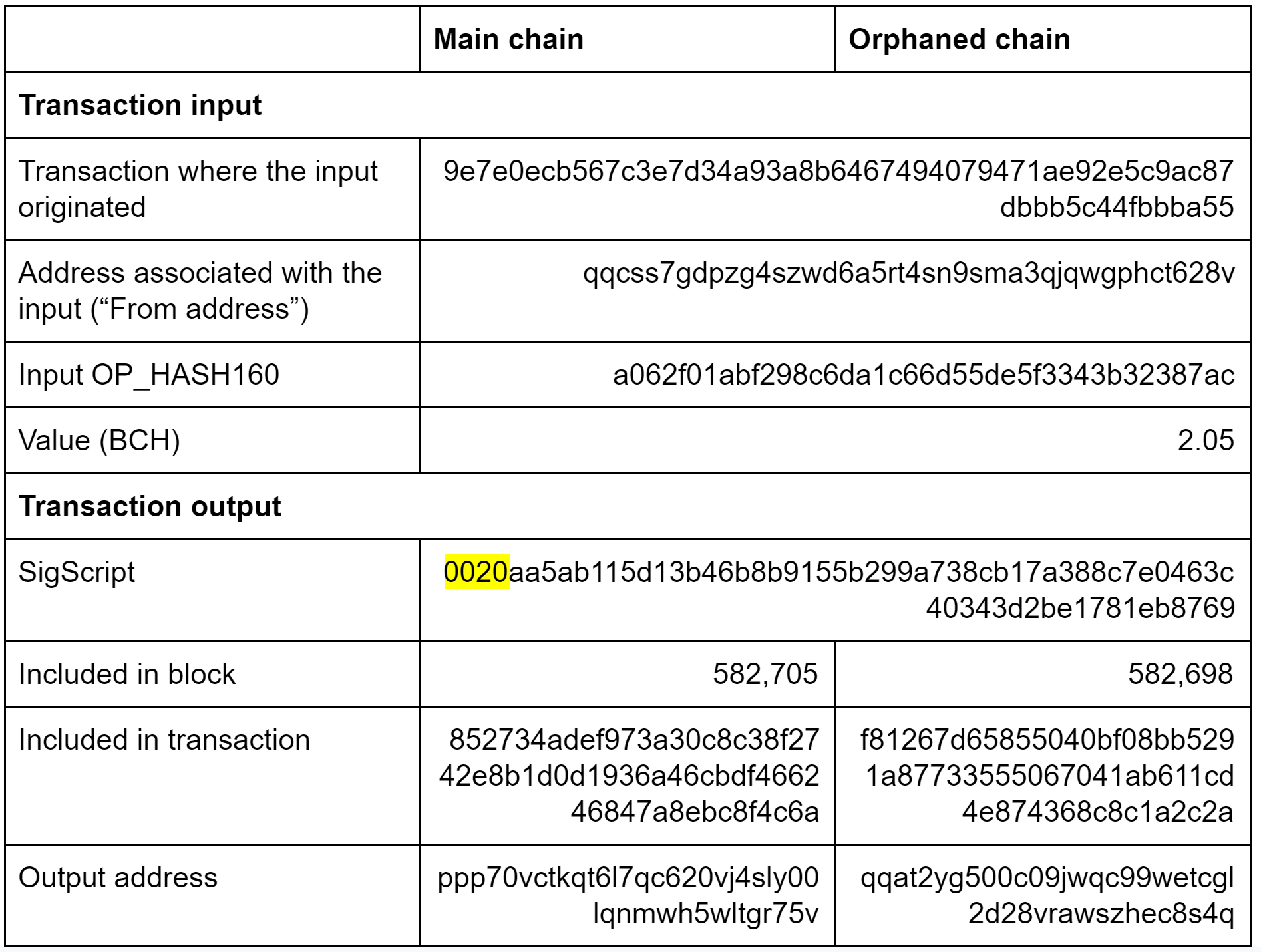
(Source: BitMEX Research)
What happened to the above outputs shares characteristics with almost all the funds in the 25 double spent transactions. Most of the outputs appear to have been double spent around block 582,705 on the main chain, around 7 blocks after the orphaned block.
The SigScript, used to redeem the transaction inputs, starts with “0020” or “0014”, highlighted in the above examples. These may relate to Segregated Witness. According to the specificationin Segregated Witness, “0014” is pushed in P2WPKH (Pay to witness public key hash) and “0020” is pushed in P2WSH (Pay to witness script hash). Therefore the redemption of these inputs may have something to do with Segregated Witness, a Bitcoin upgrade, only part of which was adopted on Bitcoin Cash.
Indeed, based on our analysis, every single input in the 25 transactions in the orphaned block 582,698 was redeemed with a Sigscript starting “0014” or “0020”. Therefore it is possible that nobody lost funds related to this chain re-organisation, other than the “attacker” or “thief” who redeemed these SegWit outputs, which may have accidentally been sent to these outputs in the first place.
As part of the Bitcoin Cash May 2019 hardfork, there was a change to allow coins which were accidentally sent to a SegWit address, to be recovered. Therefore, this may have occurred in the incident.
Allow Segwit recovery
In the last upgrade, coins accidentally sent to Segwit P2SH addresses were made unspendable by the CLEANSTACK rule. This upgrade will make an exemption for these coins and return them to the previous situation, where they are spendable. This means that once the P2SH redeem script pre-image is revealed (for example by spending coins from the corresponding BTC address), any miner can take the coins.
(Source: https://github.com/bitcoincashorg/bitcoincash.org/blob/master/spec/2019-05-15-upgrade.md)
It is possible that this 2 block re-organisation is unrelated to the empty block bug. However, the split appears to have occurred just one block after the resolution of the bug, therefore it may be related. Perhaps the “honest” miners were attempting to coordinate the spend of these outputs directly after the split, perhaps to return them to the original owners and the empty block bug messed up their timing, allowing the attacker to benefit and sweep the funds.
On the other hand, the attack is quite complex, therefore the attacker is likely to have a high degree of sophistication and needed to engage in extensive planning. Therefore, it is also possible this attack may have been effective even without the empty block bug.
Conclusion
There are many lessons to learn from the events surrounding the Bitcoin Cash hardfork upgrade. A hardfork appears to provide an opportunity for malicious actors to attack and create uncertainty and therefore careful planning and coordination of a hardfork is important. On the other hand, this empty block bug, which may be the root cause of the other 2 incidents, could have occurred at any time and trying to prevent bugs like this is critical whether one is attempting to harfork or not.
Another key lesson from these events is the need for transparency. During the incidents it was difficult to know what developers were planning, the nature of the bugs, or which chain the miners were supporting. Open communication in public channels about these issues could have been more helpful. In particular, many were unaware of an apparent plan developers and miners had to coordinate and recover lost funds sent to SegWit addresses. It may have been helpful if this plan was debated and discussed in the community more beforehand, as well as during the apparent deliberate and coordinated re-organisation. Assuming of course if there was time to disclose the latter. It may also be helpful if those involved disclose the details about these events after the fact.
The largest concern from all of this, in our view, is the deliberate and coordinated re-organisation. From one side of the argument, the funds were stolen, therefore the actions were justified in returning the funds to their “rightful owners”, even if it caused some short term disruption. However, the cash like transaction finality is seen by many, or perhaps by some, as the only unique characteristic of these blockchain systems. The ability to reverse transactions, and in this case economically significant transactions, undermines the whole premise of the system. Such behavior can remove incentives to appropriately secure funds and set a precedent or change expectations, making further reversals more likely.
For all those in the Bitcoin community who dislike Bitcoin Cash, this could be seen as an opportunity to laugh at the coin. However, although Bitcoin Cash has a much lower hashrate than Bitcoin, making this reversal easier, the success of this economically significant orchestrated transaction reversal on Bitcoin Cash is not positive news for Bitcoin in our view. In some ways, these incidents contribute to setting a dangerous precedent. It shows that it may be possible in Bitcoin. Alternatively, this could just illustrate the risks Bitcoin Cash faces while being the minority chain.
Source: BitMEX







